
Phishing Through Redirect Chains: The Threat Behind Disguised URLs
August 30, 2025Introduction
In today’s interconnected digital world, global network providers form the critical backbone of the Internet. These companies supply IP address ranges and data transit for countless businesses and end-users worldwide. Yet, when malicious activity originates from within these backbones, the same infrastructure that powers connectivity can also become a launchpad for cyberattacks.
Recent investigations by Encryptia Cloud have revealed that repeated intrusion attempts, brute-force scans, and suspicious traffic patterns are coming from IP address ranges associated with several international providers — including ACEVILLE PTE. LTD, UNMANAGED LTD, NET-3-163, and Hurricane Electric (AS6939). The attacks are global in scope, with origins traced to Singapore, the United States, Seychelles, the United Kingdom, Amsterdam, and beyond.
Case Study: ACEVILLE PTE. LTD
ACEVILLE PTE. LTD (AS139341), headquartered in Singapore, manages massive pools of IP addresses across multiple regions. While their networks are generally considered low-risk, specific ACEVILLE addresses have been actively flagged for hostile activity:
-
43.163.232.152 – over 1,100 abuse reports, brute-force attempts in the past few days.
-
43.166.240.231 – nearly 720 reports, with incidents as recent as hours ago.
-
43.165.67.57 – hundreds of brute-force complaints, with fresh activity within the last 24 hours.
These repeated abuse incidents demonstrate that parts of ACEVILLE’s infrastructure are leveraged for malicious scanning and intrusion.
Case Study: UNMANAGED LTD
UNMANAGED LTD (AS47890), based in the United Kingdom with connectivity in Romania and Western Europe, controls more than 10,000 IPv4 addresses. It has been flagged as a medium-risk ISP with a notable percentage of suspicious traffic.
-
80.94.95.222 – over 460 reports, most recently just 13 hours ago, for repeated web attack attempts and port scans.
-
80.94.93.3 – more than 300 reports, historically linked to malicious scanning.
The activity pattern shows that attackers exploit this network for brute-force and application-layer probing, making UNMANAGED LTD an active part of today’s threat landscape.
Case Study: NET-3-163
The NET-3-163 block (89.248.163.0/25), registered under IP Volume Inc. and routed via Seychelles but geolocated in Amsterdam, has become another confirmed source of hostile activity.
Despite being branded as a “research and scanning” range by the operator Recyber Project, real-world telemetry reveals repeated port scans and attack traffic. Abuse complaints highlight that this block is still frequently misused for reconnaissance and exploitation attempts.
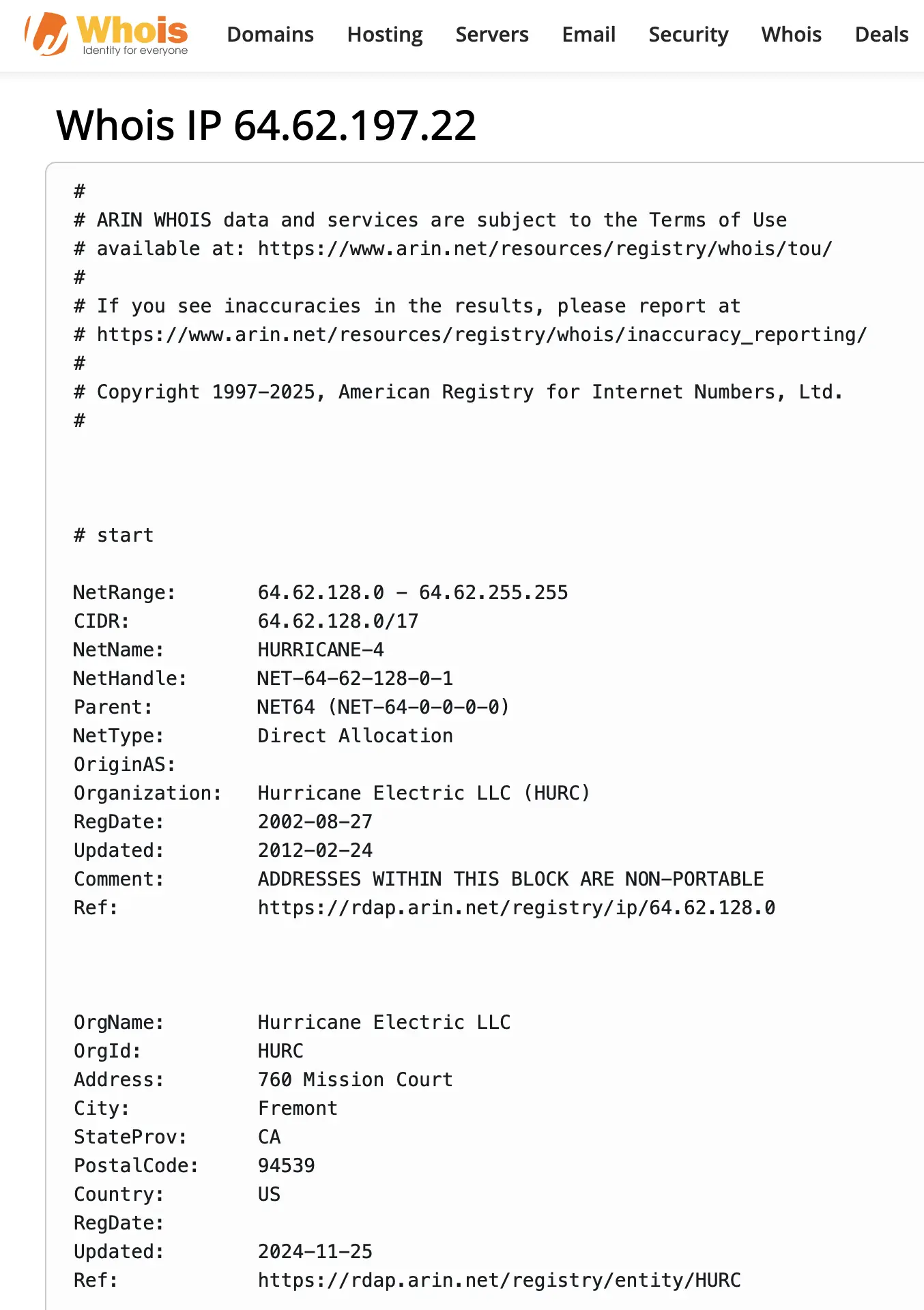
Case Study: Hurricane Electric (AS6939)
Hurricane Electric, a major U.S.-based backbone provider (AS6939), operates one of the largest IPv6 networks and provides global transit services. However, monitoring has revealed that malicious activity is also relayed through their infrastructure.
Attack logs show that adversaries take advantage of Hurricane Electric’s extensive routing reach to launch or mask brute-force attempts, port scans, and application-level probes. While not all of these activities originate from Hurricane Electric itself, the sheer scale of their network makes it a prime relay channel for hostile traffic across continents.
This underlines the growing reality: even Tier-1 backbone providers, designed to deliver speed and redundancy, can become conduits for cyber threats if abused by malicious actors.
Global Pattern of Abuse
The critical finding is not limited to one provider or country. Instead, we see a coordinated global spread of malicious origins:
-
Singapore (ACEVILLE PTE. LTD)
-
United Kingdom and Romania (UNMANAGED LTD)
-
Seychelles/Amsterdam (NET-3-163)
-
United States (Hurricane Electric)
-
Other relay nodes across Europe and Asia
This dispersion demonstrates how cybercriminals weaponize international network backbones, blending malicious traffic into normal global Internet flows.
Conclusion
The global Internet backbone was built for speed and reliability — but it is increasingly weaponized as a foundation for cyberattacks. From Singapore to the United States, from the UK to Seychelles and Amsterdam, malicious actors exploit unmanaged IP blocks and Tier-1 networks to conceal their activity.
At Encryptia Cloud, we believe transparency and vigilance are essential. By documenting these sources, reporting them, and implementing layered security measures, organizations can stay ahead of adversaries who turn the Internet’s core infrastructure into a weaponized threat surface.
Recommendations
To defend against attacks originating from backbone providers, organizations should adopt a multi-layered protection strategy:
-
Proactive IP Blocking
-
Maintain dynamic blocklists of high-risk IP ranges (ACEVILLE, UNMANAGED LTD, NET-3-163, Hurricane Electric relays).
-
Use automated firewall rules to deny repeated brute-force or scanning attempts.
-
-
Threat Intelligence Integration
-
Subscribe to global feeds that include indicators of compromise (IoCs) and malicious ASN updates.
-
Correlate logs with external threat data to detect attacks earlier.
-
-
Authentication Hardening
-
Enforce multi-factor authentication (MFA) across all user accounts.
-
Apply rate-limiting and account lockout policies for brute-force protection.
-
-
Application & Network Security
-
Deploy a Web Application Firewall (WAF) to filter malicious traffic.
-
Use intrusion detection/prevention systems (IDS/IPS) with backbone-aware threat signatures.
-
-
Abuse Reporting & Cooperation
-
Report malicious incidents to provider abuse contacts (e.g., abuse@aceville.net, abuse@unmanaged.uk, abuse@recyber.net, Hurricane Electric’s abuse desk).
-
Push upstream providers to take responsibility for compromised or misused infrastructure.
-
-
Zero Trust & Segmentation
-
Adopt a Zero Trust model to minimize lateral movement in case of compromise.
-
Segment critical assets from general network traffic to reduce exposure.
-
ENCRYPTIA Cloud
Los Angeles, CA
Stay Encrypted — Get Updates:
Support
support@encryptia.cloud
Monday - Sunday
06:00 AM - 10:00 PM
Partnerships
partners@encryptia.cloud
Monday - Friday
06:00 AM - 06:00 PM
